Azure VPN Gateway
Azure VPN
Gateway:
Azure VPN gateway is a service that uses a specific
type of virtual network gateway to send encrypted traffic between an
Azure virtual network and on-premises location over the public Internet. We can
also use VPN gateway to send an encrypted traffic between Azure virtual network
over MS network. When we create multiple connections, all VPN tunnels share the
available bandwidth.
VPN gateway is composed of 2 or more
Azure managed VMs deployed in a specific subnet called GatewaySubnet. The
Gateway VMs contains routing table and run specific gateway services.
Gateway Type determines how the
virtual network gateway will be used.
A virtual network can have
2 virtual network gateways.
1. VPN Gateway
2. Express Route
By choosing
VPN gateway type virtual network gateway, we can achieve following 3
connections.
1. Secure IPsec/IKE VPN tunnel connection between that VPN gateway
and another VPN gateway (VNet to VNet)
2. A Cross premises IPsec/IKE VPN tunnel
connection between VPN gateway and on-premises VPN device (Site to Site)
3. We can also create Point to Site VPN
connection.
Site-to-Site and ExpressRoute
can co-exist. A site-to-site can be configured as a failover path to
ExpressRoute. Also we can use Site-Site VPNs to connect to sites that aren’t
part of your network.
For
High-availability, we can create 2 VPN gateways with active-active configuration.
About
Highly Available gateway configurations - Azure VPN Gateway | Microsoft Learn
VNet-to-VNet
Global Peering using VPN Gateway
Pre-requisites:
1. EastUS VNet
2. WestUS VNet
3. VPN Gateway in EastUS VNet
4. VPN Gateway in WestUS VNet
In this section,
we will see how to connect two VNets using VPN gateway for a secure connection.
I have 2
VNETs in 2 different region, EastUs and WestUS. I want to create a connection
between these 2 using secure tunnel with encryption using VPN Gateway.
Step:1
Create 1 VPN Gateway in
EastUs with active-active mode enabled.
Step: 2
Create 1 VPN gateway in
WestUs in Active-Passive mode.
Add connections from one of the VPN gateway to establish a connection between 2 VPN gateways.
Since we are creating a connection between 2 VNETs, we need to select
VNET-to-VNET connection type. Here we are creating a connection from EastUS VPN
gateway to WestUS VNet.
Connection is still not established as we have created a connection from
one side.
Similarly we need to create a connection from WestUS VPN Gateway to EastUS
VNet.
After creating a connection from WestUS to EastUS, we can the see the
connection status as connected from both the VPN gateways.
Resources on both the VNets must be able to communicate with
each other.
Site-to-Site VPN Connection:
Pre-requisites:
1. Onprem Nework
2. WestUS VNet
3. VPN Gateway in WestUS VNet
4. Local Network Gateway to represent
Onprem Network
In this section, we are going to learn how to establish a connection
between an Azure Network and Onprem Network using Site-to-Site VPN gateway.
West US Onprem Server:
To make the onprem server as a VPN device, install below Remote Access
Roles.
Restart once the roles have been installed.
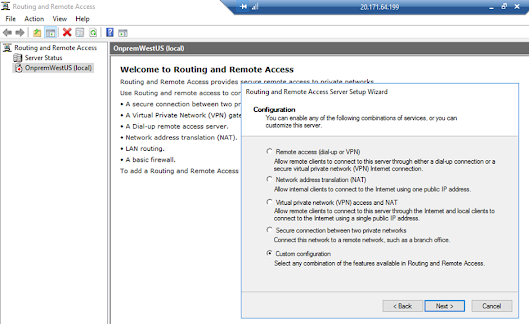
Open Routing and Remote Access window to configure.
Routing and Remote Access has been configured.
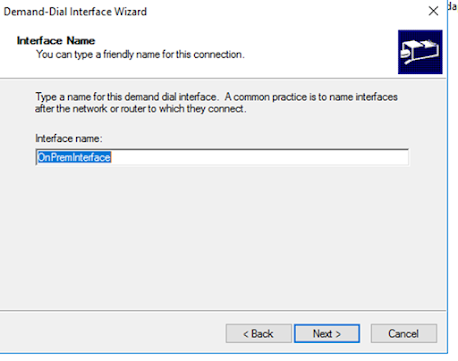
A new Demand-Dial-in interface has to be created
Going to establish a connection between West Us VNET to Onprem VPN in West
US3. I have entered West US VPN Gateway Public Address.
Network range of Azure network which we need to connect must be mentioned
here. Here I have mentioned WestUS VNet address range.
Set the preshared key for authentication
Local Network Gateway(LNG):
Need to create a LNG before establishing a connectivity between WestUS
VNet and Onprem Network.
A local network gateway to represent the on-premises site that you want to
connect to a virtual network. The local network gateway specifies the public IP
address of the VPN device and IP address ranges located on the on-premises
site. Later, create a VPN gateway connection between the virtual network
gateway for the virtual network, and the local network gateway for the
on-premises site.
20.171.64.199 is the Public IP address of Onprem VPN device and
10.0.0.0/16 is the network address range of Onprem network.
Create a Site-to-Site connection on WestUS VPN gateway to Local Network
Gateway which actually represents the Onprem VPN device.
On WestUS VNET Gateway
I’m able to connect VMs in WestUS Vnet from the On-premises network.
Site-to-Site
VPN gateway in Hub-Spoke Topology
1. Deploy a VPN device in Onpremise
network with Public Address
2. Deploy VPN gateway in Hub VNet which
is WestUS VNet
3. Deploy Local Network Gateway to represent
Onprem Network
4. Create a connection between LNG and
VPN Gateway
5. At this stage, Onprem network must be
able to reach WestUS Hub network
6. But it cannot reach Spoke VNet EastUS
VNet1 and EastUS VNet2
7. Create a Peering between Hub and 2 Spoke
VNets
Hub(WestUS)
to Spoke1 (EastUS1)
Once done,
we need to add a static routes in On-premises VPN device with EastUS VNet
range.
Once the
static routes are set for EastUS VM, you must be able to connect the VMs from East
US1 VNet.
Hub(WestUS)
to Spoke2 (EastUS2)
Repeat the
same steps as you did for WestUS to EastUs1
The connection
must be established Vice-versa as well. From Azure to On-prem networks as well.
Firewall:
I just
wanted to add a firewall in the Hub VNet(WestUSVNet) to filter the traffic
between the on-premises and Azure network.
1. Create a Subnet for firewall ‘AzureFirewallSubnet’ in WestUS VNet
Create a
firewall in Hub VNet (West US VNet)
Deploy
and configure Azure Firewall in a hybrid network by using the Azure portal |
Microsoft Learn
Add Rule
Collection to Allow Port 80 from Anywhere to East US1 network
Add Rule Collection to DENY RDP port 3389 from Anywhere to EastUS 1 Network
Created 2
Rule collections, 1 for allow and 1 for Deny
2. Now create a User Defined Routes (UDR)
just to route a traffic from the VPN Gateway subnet to the Spoke Subnet via Firewall.
This will route the traffic comes from Onprem through the VPN gateway tunnel to
the Spoke EastUS subnet via Firewall for the traffic filtration.
Created a route with destination address as a East US spoke
and next hop address as Firewall Private IP address
Associating
this route with the VPN Gateway Subnet
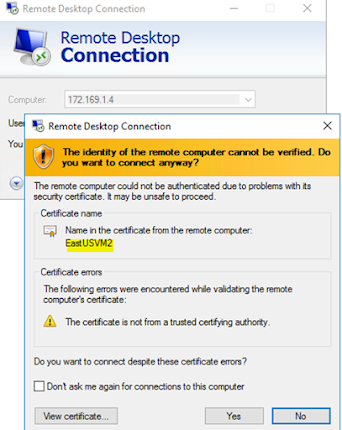
After setting
this route, I should not be able to RDP East US server (172.168.1.4)
But I
must be able to access the website via port 80





















































Comments
Post a Comment